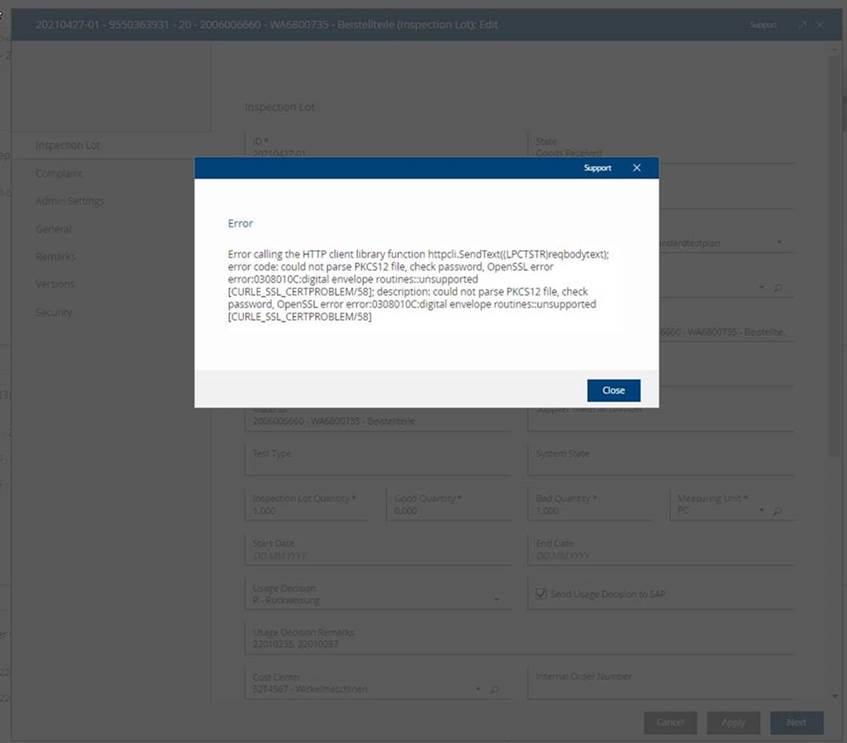
OpenSSL Error “could not parse PKCS12 file, check password”
Last update: 02 February 2023 (ck, gs, cf)
Summary
The supported encryption algorithms for PKCS12 certificates have been updated in Fabasoft Folio/eGov-Suite from 2023, which can lead to the following error message when a https call is done by the Folio Kernel, e.g. for a Mindbreeze Enterprise Search, or calls to a business application.
Solution
The error is due to the library upgrade to the more recent OpenSSL 3, which dropped support for certain cryptographic primitives commonly used in older certificates.
In the case that a specific certificate is rejected, you can check the algorithms used in the certificate file with the following command:
openssl pkcs12 -info -nokeys -nocerts -in client.p12
A typical algorithm no longer supported would be pbeWithSHA1And40BitRC2-CBC, the output would look like this (NOK):
MAC: sha1, Iteration 2048
MAC length: 20, salt length: 8
PKCS7 Encrypted data: pbeWithSHA1And40BitRC2-CBC, Iteration 2048
Certificate bag
PKCS7 Data
Shrouded Keybag: pbeWithSHA1And3-KeyTripleDES-CBC, Iteration 2048
The latest default algorithm would be Openssl AES-256-CBC looking like this (OK):
MAC: sha1, Iteration 2048
MAC length: 20, salt length: 8
PKCS7 Encrypted data: PBES2, PBKDF2, AES-256-CBC, Iteration 2048, PRF hmacWithSHA256
Certificate bag
PKCS7 Data
Shrouded Keybag: PBES2, PBKDF2, AES-256-CBC, Iteration 2048, PRF hmacWithSHA256
An old pkcs12 certificate can be brought up-to-date by exporting all parts of the certificate and re-encrypting and repackaging the file, with modern encryptions settings.
An example:
openssl pkcs12 -nokeys -in client.p12 > certs.pem
openssl pkcs12 -nocerts -in client.p12 > keys.pem
openssl pkcs12 -in certs.pem -inkey keys.pem -export -out client_new.p12 -certpbe aes-256-cbc -keypbe aes-256-cbc
Details
- The affected certificates may be the certificates loaded in the Fabasoft Folio/Fabasoft eGov-Suite installation (e.g. in the Mindbreeze Indexing Service object).
- The affected certificates may also be located on the other side, e.g. the HTTPS certificate of your business application server that interacts with Fabasoft Folio/Fabasoft eGov-Suite, if it is still using SHA-1.
- The Windows Certificate Export wizard may offer TripleDES-SHA1 as a default encryption, which is not compatible to OpenSSL 3. Select the AES256-SHA256 encryption instead.
Applies to
- Fabasoft Folio 2023 and above
- Fabasoft eGov-Suite 2023 and above