Vulnerabilities 2023
Mindbreeze security update for Basic Authentication (MINDBREEZE29751)
First published: 18 December 2023
Last update: 20 December 2023
ID: MINDBREEZE29751
Affected Components:
- Fabasoft Mindbreeze Enterprise (Linux) with active Kerberos client authentication
- Mindbreeze InSpire G7 with active Kerberos client authentication
Severity: Critical
Status: Final
CVEs: -
Original publication: https://inspire.mindbreeze.com/support/vulnerabilities/security-update-to-disable-keytab-in-jaas-login-configuration-for-basic-authentication-mindbreeze29751
Summary
When using Kerberos authentication for Mindbreeze under Linux, an attacker can in particular circumstances impersonate a user.
This vulnerability only can occur if all of the following circumstances are met:
- Mindbreeze InSpire or Fabasoft Mindbreeze Enterprise is running under Linux
- Kerberos authentication is configured
Fabasoft Mindbreeze Enterprise installed on Microsoft Windows is not affected.
Impact
After successful exploitation of this vulnerability, the attacker assimilates the same level of access as the user normally has, gaining access to index search results of this user.
Remediation
The vulnerability can be remediated by installing the hotfix listed below.
For older Fabasoft Mindbreeze Enterprise versions, a remediation by changing configuration on the Mindbreeze server is available:
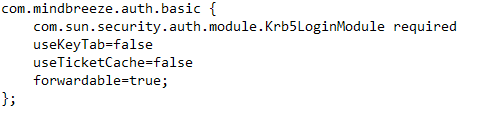
- Open the Java Kerberos configuration for editing: /etc/mindbreeze/java-krb5.conf
- Search for the Login Configuration com.mindbreeze.auth.basic
- Change the useKeyTab parameter to false:
- useKeyTab = false
- Remove the following parameter from the section:
- keyTab="${keytabpath}"
If you need further assistance, please open a Fabasoft Support Ticket.
Hotfix information
Mindbreeze provides a hotfix for the following Fabasoft Mindbreeze Enterprise version:
- Fabasoft Mindbreeze Enterprise 23.6 (23.6.3.336)
Higher versions and build numbers of Fabasoft Mindbreeze Enterprise implicitly include the hotfix.
Object list XSS security vulnerability (PDO07741)
First published: 20 July 2023 (restricted disclosure)
Last update: 29 August 2023
ID: PDO07741
Affected Components:
- Fabasoft Folio and Fabasoft eGov-Suite 2023 Update Rollup 1
- Fabasoft eGov-Suite 2023 April and June Release
Severity: CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:N Base Score: 7.3
Status: Closed
CVEs: -
Summary
During thorough testing of Fabasoft Folio/eGov-Suite a potential cross-site scripting issue has been identified concerning grouped object lists in detail view.
Only Fabasoft Folio/eGov-Suite 2023 Update Rollup 1 and Feature Track are affected, versions below Fabasoft Folio/eGov-Suite 2023 Update Rollup 1 are not affected.
Impact
While using a grouped object lists in detail view a potential cross-site scripting (XSS) vulnerability has been identified which could be exploited to inject malicious script code into the installation of Fabasoft Folio/eGov-Suite.
Remediation
The vulnerability can be remediated by installing a hotfix provided by Fabasoft.
Hotfix information
Fabasoft provides hotfixes for the following Fabasoft Folio/eGov-Suite versions:
- Fabasoft Folio/eGov-Suite 2023 Update Rollup 1 (included with 23.0.1.65)
- Fabasoft eGov-Suite 2023 April Release (included with 23.4.0.241)
- Fabasoft eGov-Suite 2023 June Release (included with 23.6.0.324)
The fix for this vulnerability is already included with the following and newer versions:
- Fabasoft Folio/eGov-Suite 2023 Update Rollup 2
- Fabasoft eGov-Suite 2023 September Release
Ghostscript pipe security vulnerability (CVE-2023-36664)
First published: 18 July 2023 (restricted disclosure)
Last update: 29 August 2023 (gs)
ID: CVE-2023-36664
Affected Components:
- Fabasoft Folio and eGov-Suite installations that use Artifex Ghostscript as a conversion tool
Severity: CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H Base Score: 7.8
Status: Open
CVEs: CVE-2023-36664
Summary
A security vulnerability has been identified and classified as CVE-2023-36664 that allows the exploitation of Artifex Ghostscript with a specifically crafted PDF document.
Impact
On installations of Fabasoft Folio/eGov-Suite that use Artifex Ghostscript as a conversion tool, it is possible that an attacker could exploit this vulnerability in Ghostscript, it is therefore recommended to perform steps to mitigate this scenario.
Remediation
Based on internal testing, installations of Fabasoft Folio/eGov-Suite 2022 Update Rollup 1 (22.0.1) and newer can successfully perform conversion operations using a version of Artifex Ghostscript that includes a fix for CVE-2023-36664.
Older versions of Fabasoft Folio/eGov-Suite using newer versions of Artifex Ghostscript abort conversion operations with an error.
If an affected system does not support a version of Ghostscript that includes a fix for CVE-2023-36664, it is possible to remove or disable Artifex Ghostscript on the conversion servers, but this operation will also affect or disable some features including the following:
- Import of files with the Fabasoft Folio Printer Ports.
- Redaction of documents in Fabasoft eGov-Suite. (Schwärzung)
- Indirect PDF conversion of documents via printing to Postscript.
Hotfix information
The following versions of Fabasoft Folio and the Fabasoft eGov-Suite can use a fixed version of Artifex Ghostscript as a conversion tool:
- Fabasoft Folio/eGov-Suite 2022 Update Rollup 1
- Fabasoft Folio/eGov-Suite 2022 Update Rollup 2
- Fabasoft Folio/eGov-Suite 2022 Update Rollup 3
- Fabasoft eGov-Suite 2022 September Release
- Fabasoft Folio/eGov-Suite 2023
- Fabasoft Folio/eGov-Suite 2023 Update Rollup 1
- Fabasoft Folio/eGov-Suite 2023 April Release
- Fabasoft Folio/eGov-Suite 2023 June Release
The following versions of Fabasoft Folio and the Fabasoft eGov-Suite can use a fixed version of Artifex Ghostscript after the installation of a relevant hotfix:
- Fabasoft Folio/eGov-Suite 2016 Update Rollup 7 (included with 16.0.11.86)
- Fabasoft Folio/eGov-Suite 2017 R1 (included with 17.4.0.73)
- Fabasoft Folio/eGov-Suite 2020 Update Rollup 5 (included with 20.1.5.81)
- Fabasoft Folio/eGov-Suite 2021 Update Rollup 3 (included with 21.1.3.82)
- Fabasoft Folio/eGov-Suite 2022 (included with 22.0.0.284)
Other versions are currently being evaluated, future updates to this article may extend the list of compatible versions.
Import path security vulnerability (eGov15419)
First published: 29 June 2023 (restricted disclosure)
Last update: 29 July 2023
ID: eGov15419
Affected Components:
- Fabasoft eGov-Suite versions up to 2023 April Release
Severity: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H Base Score: 8.8
Status: Closed
CVEs: -
Summary
In a Fabasoft eGov-Suite import feature, a normal user is able to configure any import path without restrictions, leading to a possible security issue when restricted operating system files get imported.
Only Fabasoft eGov-Suite systems are affected as this import feature is only available in Fabasoft eGov-Suite.
Fabasoft Folio is not affected by the vulnerability.
Impact
After the import, the user will have full access to the imported files. That files usually would be restricted in the original file system folder of the web server.
Due to this import the imported files may be deleted at the original location. This could lead to configuration failures or data loss on the affected webserver.
Remediation
The vulnerability can be remediated by installing a hotfix provided by Fabasoft.
Hotfix information
Fabasoft provides hotfixes for the following Fabasoft Folio/eGov-Suite versions:
- Fabasoft eGov-Suite 2019 Update Rollup 3 (included with 19.2.3.141.53)
- Fabasoft eGov-Suite 2020 Update Rollup 5 (included with 20.1.5.78.46)
- Fabasoft eGov-Suite 2021 Update Rollup 3 (included with 21.1.3.78.146)
- Fabasoft eGov-Suite 2022 Update Rollup 1 (included with 22.0.1.56.32)
- Fabasoft eGov-Suite 2022 Update Rollup 2 (included with 22.0.2.65.158)
- Fabasoft eGov-Suite 2022 Update Rollup 3 (included with 22.0.3.49.31)
- Fabasoft eGov-Suite 2022 June Release (included with 22.6.0.363.36)
- Fabasoft eGov-Suite 2022 September Release (included with 22.9.0.353.22)
- Fabasoft eGov-Suite 2023 (included with 23.0.0.227.62)
- Fabasoft eGov-Suite 2023 Update Rollup 1 (included with 23.0.1.48.27)
- Fabasoft eGov-Suite 2023 April Release (included with 23.4.0.229.7)
The vulernability is directly fixed within the releases of
- Fabasoft eGov-Suite 2023 Update Rollup 2 (and later Update Rollups and major releases)
- Fabasoft eGov-Suite 2023 June Release (and later Feature releases)
Client AutoUpdate Harmful Code Installation Vulnerability (PDO06614) 
First published: 8 May 2023 (restricted disclosure)
Last update: 4 July 2023
ID: PDO06614
Affected Components: Fabasoft Folio / Fabasoft eGov-Suite 2021 UR3, Fabasoft Folio / Fabasoft eGov-Suite 2022 (incl. all URs), Fabasoft Folio/eGov-Suite 2023 (incl. UR1), Fabasoft Cloud
Severity: CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H Total Score: 8,8 HIGH
Status: Final
CVEs: -
Summary 
A privilege escalation is possible by an intruder on a Microsoft Windows client using the Fabasoft Folio/Cloud Client AutoUpdate-Service (installed with the Fabasoft Folio Client from Fabasoft Folio/eGov-Suite 2021 or the Fabasoft Cloud Enterprise Client).
Affected Fabasoft Folio / Fabasoft eGov-Suite versions:
- Fabasoft Folio / eGov-Suite 2021 Update Rollup 3
- Fabasoft Folio / eGov-Suite 2022 (up to Update Rollup 3 and Feature Track)
- Fabasoft Folio / eGov-Suite 2023 (up to Update Rollup 1)
- Fabasoft Cloud
Versions below Fabasoft Folio / eGov-Suite 2021 Update Rollup 3 are not affected.
Linux and Apple macOS clients are not affected.
Impact 
In the case the vulnerability could be exploited, malicious software can be installed and executed on the client PC.
Remediation 
Fabasoft provides a hotfix for the Fabasoft Folio Client for the affected Fabasoft Folio / eGov-Suite versions. Please install/roll-out this hotfix immediately. If it is not possible to immediately update the Fabasoft Folio Client, see the possible workaround to disable the Fabasoft Folio Client Update Service below.
Fabasoft Cloud 
The current download of the Fabasoft Cloud Client from the Fabasoft Cloud already includes the hotfixed version of the Fabasoft Cloud Client.
If the Fabasoft Cloud Client is already installed, the update to the hotfixed version is triggered automatically.
Hotfix information Fabasoft Folio / Fabasoft eGov-Suite 
Fabasoft provides the hotfixed Fabasoft Folio Client for the affected versions in the following teamroom:
https://at.cloud.fabasoft.com/folio/public/3rz6bra2xcba40s6gt5fishghl
Only the Fabasoft Folio Client on Windows PCs needs to be updated. There is no need to update the Fabasoft Folio / eGov-Suite domain.
The following Fabasoft Folio Client build numbers include the correction:
- 23.4.0.66 and above
- 23.0.1.23 and above
- 22.9.0.75 and above
- 22.0.3.88 and above
- 21.1.3.204 and above
Workaround: Disable Fabasoft Folio Client Update Service 
The affected part of the Fabasoft Folio Client is the Fabasoft Folio Client Update Service, that is installed during the Fabasoft Folio Client installation.
This service is listed under Windows Services as
- "Fabasoft Folio Client 2023 Update Service", service name is "folioupdatepm23".
- "Fabasoft Folio Client 2022 Update Service", service name is "folioupdatepm22".
- "Fabasoft Folio Client 2021 Update Service", service name is "folioupdatepm21".
Set the service startup type to "Disabled" via Group Policy. By disabling these services, the security vulnerability cannot be exploited.
The Fabasoft Folio Client Update Service may not be installed or enabled on your clients, therefore the vulnerability cannot be exploited. Nevertheless we recommend to update the Fabasoft Folio Client.
LDAP authentication vulnerability
First published: 25 April 2023 (restricted disclosure)
Last update: 30 May 2023
ID: PDO06544
Affected Components:
- All Fabasoft Folio/eGov-Suite versions up to 2023 UR1
Severity: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N, Base Score: 9.1
Status: Closed
CVEs: -
Summary
When using the integrated LDAP authentication, an attacker can in particular circumstances impersonate a user.
Only systems using the integrated LDAP authentication feature of Fabasoft Folio are affected. It does not affect LDAP authentication via an external SAML identity provider.
The CVSS severity is reduced if LDAP authentication is only available over a local network:
CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N, Base Score: 8.1
Impact
After successful exploitation of this vulnerability, the attacker assumes all privileges of the compromised user account, with the same level of access to all objects and actions as the user normally has.
Remediation
The vulnerability can be remediated by installing one of the hotfixes listed below.
Hotfix information
Fabasoft provides hotfixes for the following Fabasoft Folio/eGov-Suite versions:
- Fabasoft Folio/eGov-Suite 2016 Update Rollup 7 (included with 16.0.11.85)
- Fabasoft Folio/eGov-Suite 2017 R1 (included with 17.4.0.71)
- Fabasoft Folio/eGov-Suite 2019 Update Rollup 3 (included with 19.2.3.141)
- Fabasoft Folio/eGov-Suite 2020 Update Rollup 5 (included with 20.1.5.78)
- Fabasoft Folio/eGov-Suite 2021 Update Rollup 3 (included with 21.1.3.77)
- Fabasoft Folio/eGov-Suite 2022 (included with 22.0.0.283)
- Fabasoft Folio/eGov-Suite 2022 Update Rollup 1 (included with 22.0.1.55)
- Fabasoft Folio/eGov-Suite 2022 Update Rollup 2 (included with 22.0.2.63)
- Fabasoft Folio/eGov-Suite 2022 Update Rollup 3 (included with 22.0.3.48)
- Fabasoft Folio/eGov-Suite 2022 September Release (included with 22.9.0.352)
- Fabasoft Folio/eGov-Suite 2023 (included with 23.0.0.226)
- Fabasoft Folio/eGov-Suite 2023 Update Rollup 1 (included with 23.0.1.18)
- Fabasoft Folio/eGov-Suite 2023 April Release (included with 23.4.0.228)
HTML Injection and Cross-Site Scripting in Time Travel Feature (eGov14917)
First published: 23 January 2023
Last update: 25 January 2023
ID: eGov14917
Affected Components:
- Fabasoft eGov-Suite 2019
- Fabasoft eGov-Suite 2020
- Fabasoft eGov-Suite 2021
- Fabasoft eGov-Suite 2022
Severity: CVSS:3.1/AV:A/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:N, Base Score: 8.1
Status: Final
CVEs: -
Summary
An input field of the Time Travel feature in the Fabasoft eGov-Suite is vulnerable to HTML injection and stored cross-site scripting.
To exploit this vulnerability an attacker has to be authenticated as a valid user.
The vulnerability only concerns Fabasoft eGov-Suite, but not Fabasoft Folio.
Impact
An attacker could insert HTML or JavaScript code into the affected Time Travel input field of an object (e.g. document). If another user has access to this object and opens the Time Travel feature, the inserted HTML or JavaScript code may be executed in the user’s web browser.
Remediation
The vulnerability can be remediated by installing one of the hotfixes listed below.
Hotfix information
Fabasoft provides hotfixes for the following Fabasoft eGov-Suite versions:
- Fabasoft eGov-Suite 2022 September Release
- Fabasoft eGov-Suite 2022 June Release
- Fabasoft eGov-Suite 2022 Update Rollup 2
- Fabasoft eGov-Suite 2021 Update Rollup 3
- Fabasoft eGov-Suite 2020 Update Rollup 5
The fix is already included starting with the following Fabasoft eGov-Suite build numbers:
- Fabasoft eGov-Suite 2023
- Fabasoft eGov-Suite 2022 Update Rollup 3
- Fabasoft eGov-Suite 2022 September Release from build 22.9.0.344.19
- Fabasoft eGov-Suite 2022 June Release from 22.6.0.363.035
- Fabasoft eGov-Suite 2022 Update Rollup 2 from 22.0.2.56.149
- Fabasoft eGov-Suite 2021 Update Rollup 3 from 21.1.3.63.142
- Fabasoft eGov-Suite 2020 Update Rollup 5 from 20.1.5.75.44
- and any later major releases and Update Rollups.
